 |
| Microsoft Windows logs sent to remote linux syslog server over secure tunnel |
I have been sending system log entries from as many of my servers and devices as I can to a remote central syslog (rsyslog) server running on one of my Linux VPS cloud virtual machines for quite a while now. As described in my post "Secure Remote Logging to Central Log Server Using RSYSLOG on CentOS 6 / CentOS 7 and stunnel", I use Michał Trojnara's stunnel tool to securely forward TLS encrypted log entries to the VPS since the log entries travel over the internet to the VPS and I did not want them to go over in clear-text. I have had great fun and success in sending system logs from diverse systems this way, including various flavors of Linux, Solaris 11 (SunOS 5.11), Mac OS X El Capitan, DD-WRT router firmware, FreeBSD based pfSense firewall, AdTrap Internet Ad Blocking Device, Sophos UTM 9 gateway, ClearOS gateway, and even OpenVMS 7.1 VAX on Digital VAXservers and more.
I recently configured Microsoft Windows 10 laptops in the house to also send on their logs to the remote central rsyslog server on the VPS. Here is my attempt to jot down what I did.
Step 1 - Download, Install and Configure NXLog for Windows
NXLog Community Edition is an excellent free tool to collect logs from Windows and forward them in unix-style syslog format to any desired syslog/rsyslog server.
First, determine if you are using the 32-bit or 64-bit edition of the Windows operating system. You can follow Microsoft's guide to find out.
Then, download the NXLog Community Edition Windows installer from here and install it with all default options.
Once NXLog Community Edition is installed, we need to edit NXLog's configuration file, which unfortunately resides in the protected C:\Program Files (x86)\nxlog\conf folder (or C:\Program Files\nxlog\conf on 32-bit Windows installations). Click on the desktop Start button, and type in Notepad in the search box at the bottom of the Start menu. When "Notepad" appears in the search results at the top, right-click on it and choose "Run as administrator".
 |
| Launch Windows Notepad as Administrator |
Then click "Yes" on the UAC (User Account Control) dialog box or provide the credentials of an Administrator account if asked, and Notepad should launch with administrator privileges.
Use Notepad menu's File -> Open to navigate to C:\Program Files (x86)\nxlog\conf (or C:\Program Files\nxlog\conf on 32-bit Windows installations) and open the file nxlog.conf. Replace the entire contents of this file with the following:
If you are on a 32-bit Windows platform, go ahead and follow the instructions at the top of the file to un-comment the line "define ROOT C:\Program Files\nxlog" and comment out the line "define ROOT C:\Program Files (x86)\nxlog".
The "<Input watchfile>" blocks in nxlog.conf allow you to specify additional log files to monitor. This feature is useful in monitoring the log files written by many applications into the Windows temporary file folder. I typically re-point Windows system and user temporary file directories to C:\TEMP\WINTEMP to keep them out of the operating system root folder. To do this, I create the C:\TEMP\WINTEMP directory manually first, and then remove user-specific TEMP and TMP environment variables for all users and change the system TEMP and TMP environment variables to C:\TEMP\WINTEMP using Control Panel -> System -> Advanced System Settings ->Advanced tab -> Environment Variables. If you do not want to do all this temporary file re-pointing stuff, change the "File" parameter in the "<Input watchfile>" block in nxlog.conf to monitor log files in the default Windows temporary file location using the correct escaped back-slash syntax, i.e.
File 'C:\\WINDOWS\\TEMP\\*.log'
Save nxlog.conf and restart the nxlog service for the new configuration to take effect. Use Control Panel -> Administrative Tools -> Services, right-click on nxlog and choose Restart.
 |
| Restart NXLog Service on Windows after modifying nxlog.conf |
NXLog is now configured to forward Windows System and Event log entries at real-time over TCP/IP to port 65514 on localhost.
Step 2 - Download, Install and Configure stunnel for Windows
As I mentioned at the beginning of this post, my syslog server consists of a stunnel endpoint that forwards incoming log data to a rsyslog server. This allows me to send log data securely over the internet to the stunnel endpoint which forwards it locally to rsyslog running on the the same box. All this is described "Secure Remote Logging to Central Log Server Using RSYSLOG on CentOS 6 / CentOS 7 and stunnel". I assume a similar setup already present for the following; if you do not have one or are okay with cleartext transmission, you can ignore this step and simply edit the <Output syslogout> section of nxlog.conf to point directly to your syslog server IP and Port (the port number for syslog is usually 514), restart the NXLog service and be done with it, no need to read more.
In the previous step, NXLog was configured to send Unix-style syslog data over TCP/IP to localhost 127.0.0.1 and Port 65514. Now in this step, we install stunnel for Windows and configure it to accept the log data from NXLog locally on port 65514 and send it encrypted and secured to the remote syslog server's stunnel end-point on port 65515.
First, head over to the official stunnel distribution website, download the Win-32 installer and install stunnel. I installed it with the "All Users" option.
Second, we need to install stunnel as a Windows service. To do this, open up a command prompt with administrator privileges and execute the following two commands:
cd "c:\Program Files (x86)\stunnel\bin"
stunnel -install
First, head over to the official stunnel distribution website, download the Win-32 installer and install stunnel. I installed it with the "All Users" option.
Second, we need to install stunnel as a Windows service. To do this, open up a command prompt with administrator privileges and execute the following two commands:
cd "c:\Program Files (x86)\stunnel\bin"
stunnel -install
You should see a pop-up confirming that the stunnel service was installed.
Third, we need to configure stunnel. From the Windows desktop Start menu, navigate to All Programs -> stunnel Allusers -> Edit stunnel.conf. Confirm the UAC access warning, and replace the contents of stunnel.conf with the following, replacing remote-stunnel-syslog-server-IP:Port with the IP address and port number of the stunnel endpoint on your remote syslog server.
client = yes
fips = no
[nxlog-syslog-to-vps]
accept = 127.0.0.1:65514
connect = remote-stunnel-syslog-server-IP:Port
Save stunnel.conf and exit Notepad.
Fourth, start up the stunnel Windows service from the desktop Start button navigating to All Programs -> stunnel Allusers -> stunnel Service Start. After confirming the UAC warning, you should get a pop-up confirmation of the service having been started.
 |
| stunnel Windows service started |
Fifth, check the stunnel service "Stunnel TLS Wrapper" from Control Panel -> Administrative Tools -> Services to make sure the stunnel service is configured for Automatic startup type and is in the Running status.
 |
| stunnel for Windows service |
At this point, all your Windows system and event log entries will be forwarded to the remote server's stunnel endpoint and then to the remote syslog server.
If it is not working as expected, debugging is easily done by stopping the service and starting stunnel in GUI mode from desktop Start menu -> All Programs -> stunnel Allusers -> stunnel GUI Start. This opens up a log file on screen. On a working system, the logs show that stunnel has accepted a connection from localhost (from NXLog) and is connected to the remote host (stunnel endpoint of remote syslog server).
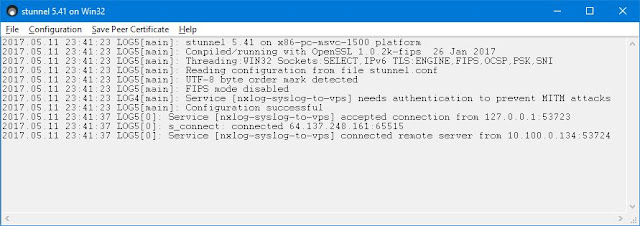 |
| stunnel for Windows GUI mode log file |
I find this method of using stunnel to enctrypt syslog entries to a remote server simpler than configuring TLS certificates and transports in syslog configuration files themselves. Share your thoughts and experiences in achieving similar results in comments below.
Download
You can download the versions of NXLog and stunnel that are current at the time of writing from my google drive here.
Download
You can download the versions of NXLog and stunnel that are current at the time of writing from my google drive here.