I am documenting my experience in installing and configuring DLNA UPnP LXiMedia Server on a PC running CentOS 7 currently running kernel 3.10.0-514.10.2.el7.x86_64 #1 SMP Fri Mar 3 00:04:05 UTC 2017. I was able to make available music and video from an external Samba share connected to this Linux box running LXiMedia Server to multiple devices in our home, including iPhone, iPad, Android phone, Roku streaming player, Windows PC, Macbook Pro, iMac, etc.
INSTALLING LXi Media Server
1) Install required packages. Run as root (or use sudo).
To install C, C++ and development tools:
# yum -y groups mark install "Development Tools"
# yum -y groups mark convert "Development Tools"
# yum -y group install "Development Tools"
To install the additional packages needed by LXiMedia:
# wget http://li.nux.ro/download/nux/dextop/el7/x86_64/nux-dextop-release-0-1.el7.nux.noarch.rpm
# yum localinstall -y nux-dextop-release-0-1.el7.nux.noarch.rpm
# rpm -import http://li.nux.ro/download/nux/RPM-GPG-KEY-nux.ro
# yum -y install debhelper dpkg-dev bash doxygen gcc make binutils-dev cmake3 uuid-devel vlc vlc-devel
For example, download the LXiMedia 0.5.0 source (or from the direct link).
3) Change to the extracted source files directory and build using cmake3 and make.
# cd lximediaserver-0.5.0
# cmake3 -DCMAKE_BUILD_TYPE=Release
# make
A successful build completes with the message "[100%] Built target lximediaserver".
3) Launch the lximediaserver
# ./lximediaserver
This will return to the prompt with lximediaserver running as a daemon (check with "ps -aef | grep lximediaserver")
CONFIGURING LXi Media Server
Configure lximediaserver using the web interface presented by default on port 4280. For example, if the CentOS server is 10.100.0.10, launch a web browser on any machine on the same subnet and visit the URL http://10.100.0.10:4280.
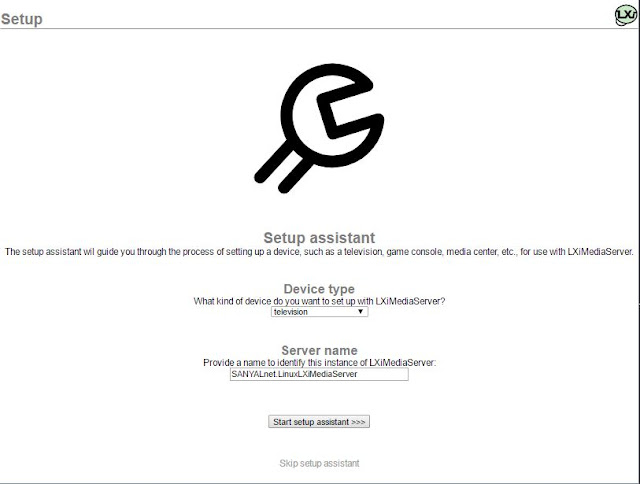 |
| LXi Media Server initial screen |
The initial setup screen looks like this. Click on the barely visible "Skip setup assistant" link at the bottom to get to the main setup screen. If you do not see the "Skip setup assistant" link at the bottom, kill and restart the lximediaserver process and refresh your web browser.
 |
| LXi Media Server Settings Screen |
You will now be presented with the main LXi Media Server Settings screen.
Add all the directories that contain your music, video and picture media one by one to the Folders box, clicking Append to add new subdirectories to the full path name of each and Save when done. This is an unusual way to specify the full pathnames for the media folders, but it works.
 |
| Adding media folders to LXi Media Server |
You can also adjust the encoding settings depending on how powerful your CPU is and your home network bandwidth.
Share your experience and tips for LXi Media server in comments below.
Share your experience and tips for LXi Media server in comments below.