 |
| pfSense Dashboard |
The amazing pfSense Community Edition forms the first of my three-layer home internet security firewall and gateway. I have a dual-WAN setup with subscriptions to both Verizon FiOS and Comcast Xfinity, with the LAN side feeding into a Sophos UTM 9 which is further protected by ClearOS.
I run pfSense in a virtual machine. However, there are excellent dedicated firewall routers with pfSense preinstalled available that you can simply plug in between your WAN and LAN, like this one (includes my Amazon affiliate link):
I am a huge fan of blocklists and over the years settled down to a functional set of IP and DNSBL blocklists used with the wonderful pfBlockerNG package on my installation of pfSense Community open-source router firewall.
I have completely disabled IPv6; all of the following blocklists are for IPv4, and for DNSBL, domain names.
IP BLOCKLISTS
For the IP blocklists, the top-level blocklist groups are Level-1, Level-2, Level-3, Level-4 and SANYALnet.
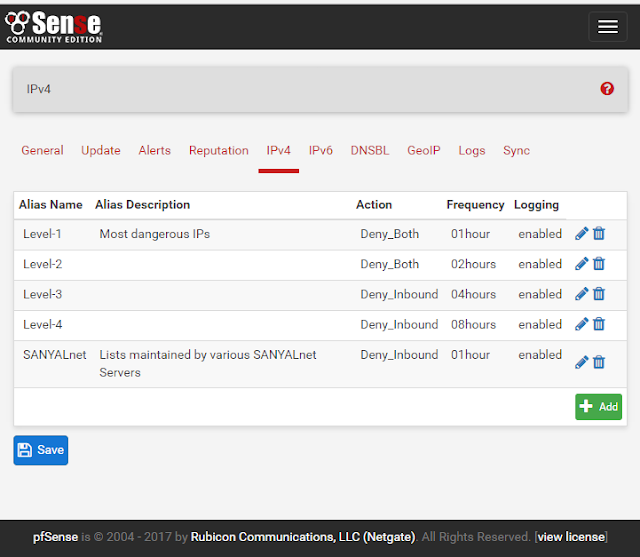 |
| pfBlockerNG on pfSense - top level IP (IPv4) blocklist groups |
Level-1 IP Blocklist
 |
| pfBlockerNG Level-1 IP Blocklist sources |
Incoming as well as outgoing connections from / to blocklisted IPs are blocked for these highest risk IP addresses. Of particular concern in modern times are the command-and-control (CNC) botnets particularly infecting digital security and surveillance systems, cameras, routers, televisions, DVD players and all sorts of devices making up the Internet of Things (IoT). The Level-1 IP BL is updated every hour, and the group members are:
- https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset
https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt(removed, no longer works)- https://rules.emergingthreats.net/blockrules/compromised-ips.txt
- https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt
- http://www.abuseat.org/iotcc.txt
- https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/cybercrime.ipset
Level-2 IP Blocklist
In addition to IoT C&C botnets, the other primary threat today is from Ransomware. I only have Firehol Level 2, Ransomware Tracker IP blacklists from abuse.ch including CryptoWall, Locky, TeslaCrypt, TorrentLocker C&C and Payment, and Zeus tracker and ci badguys IP deny blocklists at my level 2, which is also configured to block all outgoing as well as incoming connections. Level 2 IP blocklists are updated every 2 hours.
 | |
|
- https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level2.netset
- http://cinsscore.com/list/ci-badguys.txt
- https://ransomwaretracker.abuse.ch/downloads/CW_PS_IPBL.txt
- https://ransomwaretracker.abuse.ch/downloads/LY_PS_IPBL.txt
https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt(removed, no longer works)- https://ransomwaretracker.abuse.ch/downloads/TC_PS_IPBL.txt
- https://ransomwaretracker.abuse.ch/downloads/TL_C2_IPBL.txt
- https://ransomwaretracker.abuse.ch/downloads/TL_PS_IPBL.txt
- https://zeustracker.abuse.ch/blocklist.php?download=badips
Level-3 IP Blocklist
 |
| pfBlockerNG Level-3 IP Blocklist sources |
IP addresses in my level 3 blocklist are denied on the incoming side only, i.e. I allow connections initiated from inside my home LAN out to these IPs to go through. The level 3 IP blacklist addresses are updated every 4 hours. The sources are:
- https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level3.netset
- http://danger.rulez.sk/projects/bruteforceblocker/blist.php
- http://www.openbl.org/lists/base_7days.txt
- https://lists.blocklist.de/lists/all.txt
- http://malc0de.com/bl/IP_Blacklist.txt
- https://feodotracker.abuse.ch/blocklist/?download=ipblocklist
Level-4 IP Blocklist
 |
| pfBlockerNG Level-4 IP Blocklist sources |
There are only a couple of blacklist sources for my level 4, including Firehol Level 4, and Malware Domain List IP addresses the equivalent domains of which are also included in my list of DNSBL lists separately. Level 4 is configured to block inbound connections only and updated every 8 hours.
- https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level4.netset
- http://www.malwaredomainlist.com/hostslist/ip.txt
SANYALnet IP Blocklist
 |
| pfBlockerNG SANYALnet IP Blocklist sources |
The SANYALnet group is a collection of blocklists I maintain myself based on the brute force attacks and intrusion attempts logged by my own servers. This group is updated every hour to minimize on-going attacks. Please note: these are my own servers hosted on a super-cheap VPS service and up-times are not the best :)
- http://sanyalnet-cloud-vps.freeddns.org/blocklist.txt [status]
- http://sanyalnet-cloud-vps.freeddns.org/mirai-ips.txt [status]
- http://sanyalnet-cloud-vps2.freeddns.org/blocklist.txt [status]
- http://microvax3100-80.duckdns.org/blocklist.txt (experimental) [status]
pfBlockerNG DNSBL Feeds
 |
| pfBlockerNG DNSBL Feeds DNS Groups |
The DNSBL configuration redirects domain name lookups for blocked domains to my own "httpd410server" DNS sinkhole.
I have grouped the DNSBL feeds into three groups.
Zero-day Threat Domain Blocklist Group
 |
| pfBlockerNG DNSBL Zero-Day Threat Domain Blocklist |
- https://openphish.com/feed.txt
General Domain Blocklist Group
 |
| pfBlockerNG DNSBL General Domain Blocklist Group |
This group contains a collection of malware, ransomware, adware, spyware, tracker and generally undesirable domain blocklists updated once every day. This includes advertising services, thus making my pfSense firewall an effective ad blocker for all devices on my entire home network.
I turned the Eladkarako and Immortal Long Lived Malware Domains blocklists off because they were too generic and were blocking too many websites used by folks in my home. If you wish, you can turn them on for a more secure DNSBL at the cost of filtering out some websites that are otherwise useful.
- https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt
- http://www.malware-domains.com/files/justdomains.zip
- https://isc.sans.edu/feeds/suspiciousdomains_Low.txt
- https://isc.sans.edu/feeds/suspiciousdomains_Medium.txt
- https://isc.sans.edu/feeds/suspiciousdomains_High.txt
- https://raw.githubusercontent.com/Dawsey21/Lists/master/main-blacklist.txt
- http://s3.amazonaws.com/lists.disconnect.me/simple_malvertising.txt
- http://s3.amazonaws.com/lists.disconnect.me/simple_ad.txt
- http://s3.amazonaws.com/lists.disconnect.me/simple_tracking.txt
- http://raw.githubusercontent.com/quidsup/notrack/master/trackers.txt
- Use with care: http://raw.githubusercontent.com/eladkarako/hosts.eladkarako.com/master/_raw__hosts.txt
- Use with care: http://mirror1.malwaredomains.com/files/immortal_domains.txt
Hosts File Format Blocklists
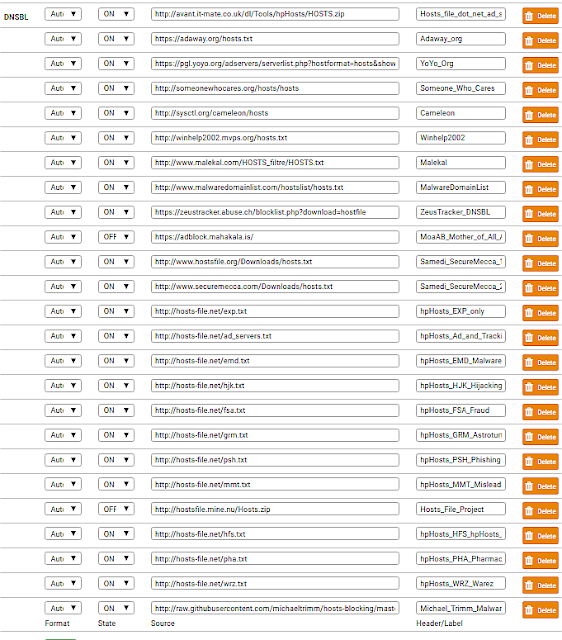 |
| pfBlockerNG DNSBL General hosts File Format Blocklist Group |
- https://raw.githubusercontent.com/StevenBlack/hosts/master/alternates/fakenews-gambling-porn/hosts
- http://avant.it-mate.co.uk/dl/Tools/hpHosts/HOSTS.zip
- https://adaway.org/hosts.txt
- https://pgl.yoyo.org/adservers/serverlist.php?hostformat=hosts&showintro=0&startdate%5Bday%5D=&startdate%5Bmonth%5D=&startdate%5Byear%5D=&mimetype=plaintext
- http://someonewhocares.org/hosts/hosts
- http://sysctl.org/cameleon/hosts
- http://winhelp2002.mvps.org/hosts.txt
- http://www.malekal.com/HOSTS_filtre/HOSTS.txt
- http://www.malwaredomainlist.com/hostslist/hosts.txt
- https://zeustracker.abuse.ch/blocklist.php?download=hostfile
- http://www.hostsfile.org/Downloads/hosts.txt
- http://www.securemecca.com/Downloads/hosts.txt
- http://hosts-file.net/exp.txt
- http://hosts-file.net/ad_servers.txt
- http://hosts-file.net/emd.txt
- http://hosts-file.net/hjk.txt
- http://hosts-file.net/fsa.txt
- http://hosts-file.net/grm.txt
- http://hosts-file.net/psh.txt
- http://hosts-file.net/mmt.txt
- http://hosts-file.net/hfs.txt
- http://hosts-file.net/pha.txt
- http://hosts-file.net/wrz.txt
- http://raw.githubusercontent.com/michaeltrimm/hosts-blocking/master/_hosts.txt
pfBlockerNG DNSBL Custom Domain Whitelist
 |
| pfSense pfBlockerNG DNSBL Custom Domain Whitelist |
Sometimes a domain blocklist included in pfSense pfBlockerNG DNSBL configuration will block URLs that you find useful and want to visit. Instead of digging through the logs to figure out which list is blocking your desired domain and disabling the entire list, you can simply add the domains that should not be blocked in the nifty Custom Domain Whitelist feature included as part of the DNSBL configuration.
Consolidated IP and DNSBL Blocklists
I make consolidated IP address and Domain Name blocklists available for free public use from my VPS at the following links; feel free to use them.- Consolidated IP Address Blocklist
- Consolidated Domain Name Blocklist (This is NOT pfBlockerNG compatible, but useful for folks running dnsmasq daemon on their internet gateway)
pfSense pfBlockerNG in Action
With the pfBlockerNG setup for IP and DNS Blocklists described above, I do see domains and IPs blocked all the time - here is a typical example of pfBlockerNG's "Alert" screen that shows the last 25 IP addresses and domains blocked at the time of writing:
 |
| pfSense pfBlockerNG Active Blocked IP Addresses and Domains |
A pfBlockerNG force reload log looks like this:
Hope you find this useful and please share the IP and domain blocklists you have found and use in comments below.
No comments:
Post a Comment
"SEO" link builders: move on, your spam link will not get posted.
Note: Only a member of this blog may post a comment.