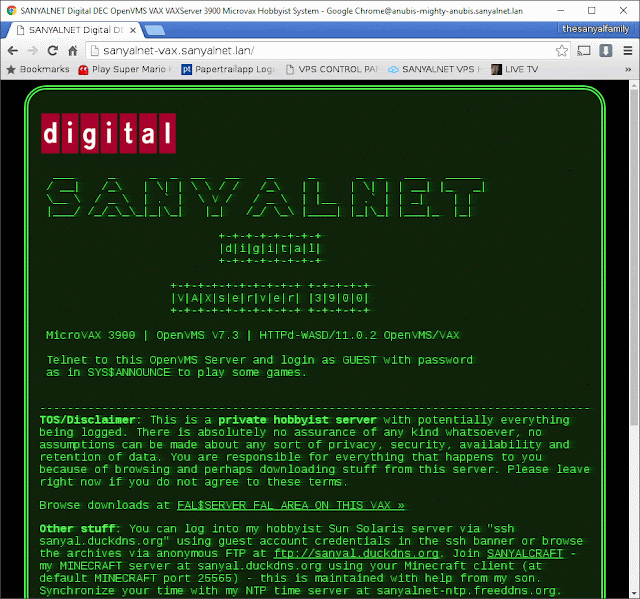
WASD 11.0.2 Web Server on DEC Digital VAX 3900 OpenVMS VAX 7.3
This is what I did to bring up a minimal WASD web server on my VAX running OpenVMS 7.3. I did manage to have my website run from a separate user account than WASD and even link to my FAL$SERVER directory for HTTP access in addition to DECNET access to my FAL server.
Preparation
 |
| WASD 11.0.2 Web Server on DEC Digital VAX 3900 OpenVMS VAX 7.3 |
This is what I did to bring up a minimal WASD web server on my VAX running OpenVMS 7.3. I did manage to have my website run from a separate user account than WASD and even link to my FAL$SERVER directory for HTTP access in addition to DECNET access to my FAL server.
First, follow this post to install CPQ-VAXVMS-SSL-V0101-B-1.PCSI-DCX_VAXEXE and VMSPORTS-VAXVMS-ZLIB-V0102-8-1.ZIP. You should go ahead and follow the entire post to install CURL for OpenVMS VAX 7.3 anyway, CURL is a pretty useful tool to have on your VAX. The SSL version this obtained will remain unused by WASD but the installer will proceed. The installer will use ZLIB.
Then head to the WASD VMS Web Services Download Page and download the latest version for WASD for OpenVMS VAX 7.3. I downloaded the latest version at the time of writing: WASD1102.ZIP. You can also grab it from QCOCAL over HECNET or now by internet, thanks to WASD, from here.
Create a new directory WASD_ROOT on a device with at least 630,000 blocks free. I created DUA2:[WASD_ROOT], and this post is written to reflect that. Adjust according to your needs.
Unzip the downloaded installation ZIP file into the new directory and run the install command file using @INSTALL. Follow the prompts and answer questions taking cues from a log the installation procedure I captured and saved here to build and install the initial working configuration of WASD.
When the install.com procedure completes, start up WASD using @DUA2:[WASD_ROOT.STARTUP]STARTUP.COM and point a web-browser on another computer on your subnet to your VAX. You should see the default WASD web-site with no further configuration needed for the out-of-the-box installation. Use CTRL-Y to exit as instructed.
Set up a different http server root
Create another new directory to hold your web-site and a top-level web server document root under that. I first created DUA2:[WEBROOT] and then a [.HTML] directory under it. Set global read and execute permissions on this directory using
$ SET FILE/PROT=(W:RE) DUA2:[000000]WEBROOT.DIR
$ SET FILE/PROT=(W:RE) DUA2:[000000.WEBROOT.HTML]
Add a simple test HTML file under DUA2:[WEBROOT.HTML]INDEX.HTML - this will be returned to your browser after configuration is complete. The following INDEX.HTML will do fine as your initial test page:
<html><head><title>WASD OpenVMS/VAX</title></head><body><p>TEST</p><p><a href="/falserver/">FAL AREA ON THIS VAX »</a></p></body></html>
Copy over the EXAMPLE configuration files to DUA2:[WASD_ROOT.LOCAL]:
$ COPY DUA2:[WASD_ROOT.EXAMPLE]*.CONF DUA2:[WASD_ROOT.LOCAL]
Then change to the .LOCAL directory.
Setup Local Configuration of WASD
In the .LOCAL directory, edit WASD_CONFIG_MAP.CONF and delete all lines. Add the following few lines only.
Edit WASD_CONFIG_GLOBAL.CONF and replace with the following contents. This is intended to bolster security by turning off scripting support, narrowing allowed default HTML files to index.html, enable reverse DNS lookup, add missing MIME types for directory displays etc. (DIFF with the .EXAMPLE version of WASD_CONFIG_GLOBAL.CONF to see the differences).
Edit WASD_CONFIG_SERVICE.CONF and enable only HTTP port 80 on the WAN address for our minimal installation.
No other configuration files need to be manipulated for our minimal WASD web server configuration.
Configure Logicals and Startup at Boot
Define the following two logicals manually for now:$ DEFINE /SYSTEM /EXEC /TRANSLATION=CONCEALED WEB_ROOT DUA2:[WEBROOT.HTML.]
$ define /system/exec /TRANSLATION=CONCEALED falserver dua2:[fal$server.]
Also add them to system boot-time startup definitions. Edit your SYS$MANAGER:SYSTARTUP_VMS.COM and add the following where you define your site-specific startup scripts:
$! Start up the web server
$ DEFINE /SYSTEM /EXEC /TRANSLATION=CONCEALED WEB_ROOT DUA2:[WEBROOT.HTML.]
$ define /system/exec /TRANSLATION=CONCEALED falserver dua2:[fal$server.]
$ @DUA2:[WASD_ROOT.STARTUP]STARTUP.COM
$!
Note: Since you already installed the SSL and ZLIB applications at the beginning, you should already have the following startup commands executing before starting the WASD web server:
$ @sys$startup:ssl$startup.com
$ @sys$startup:gnv$zlib_startup.com
Also, my FAL directory is at DUA2:[FAL$SERVER] and that is what the falserver logical above reflects. Obviously you need to adjust for your FAL Server location.
Important: Do not miss the dot before the closing square brackets in the logicals. As a quick test, commands like DIR WEB_ROOT:[000000] and DIR FALSERVER:[000000] need to resolve to the directories correctly. Examples of what I get:
DUA2:[WASD_ROOT.LOCAL] DIR WEB_ROOT:[000000]
Directory WEB_ROOT:[000000]
DIGITAL.PNG;1 FAVICON.ICO;1 HTML.TAR;1 INDEX.HTML;22
STYLES.DIR;1
Total of 5 files.
DUA2:[WASD_ROOT.LOCAL] DIR FALSERVER:[000000]
Directory FALSERVER:[000000]
INFO.TXT;1 INTRUSIONS.TXT;11 INTRUSIONS.TXT;10 INTRUSIONS.TXT;9
KRB.DIR;1 NET$SERVER.LOG;48 NODENAMES.DAT;172 NODENAMES.DAT;171
SOFTWARE-DOWNLOADS.DIR;1
Total of 9 files.
Stop WASD and restart it:
$ @DUA2:[WASD_ROOT.STARTUP]SHUTDOWN.COM
$ @DUA2:[WASD_ROOT.STARTUP]STARTUP.COM
Again point a web-browser (remember to Shift+Reload on your browser to force a fresh non-cached request) on another computer on your subnet to your VAX. You should now see tiny test html page. Clicking on the FAL AREA link should show the files in your FAL$SERVER directory.
The only stumble I had was with file and directory permissions. If you get "ERROR 403 - The requested action is not permitted." or "ERROR 404 - The requested resource could not be found." errors, remember WASD needs to be able to reach and read the HTML files for your website in a different account, as well as FAL area files, and make sure they at least have READ privileges for the World:
$ SET FILE/PROT=(W:R) DUA2:[WEBROOT...]*.*
$ SET FILE/PROT=(W:R) DUA2:[FAL$SERVER...]*.*
WASD writes its httpd Access Log to the .LOG directory wasd_root:[log]. Example:
DUA2:[WASD_ROOT.LOCAL] dir wasd_root:[log]
Directory WASD_ROOT:[LOG]
.WWW_HIDDEN;1 LOCALHOST_80_20161031_ACCESS.LOG;1 README.HTML;1
SANYALNET-VAX-SANYAL_80_20161031_ACCESS.LOG;1
Total of 4 files.
The WASD install script created two accounts - one to run the WASD server process, and a "nobody" account to run scripts from. In addition, I created the WEBROOT account as the root html directory. I modified the account expiration and password lifetimes so that their passwords do not expire. I also made the WEBROOT account captive with no NETMBX privilege - the only purpose of this account is to be a holding place for HTML files served by WASD web-server. Here are the account characteristics I see:
DUA2:[WASD_ROOT.LOG] cd sys$system
SYS$SYSROOT:[SYSEXE] mc authorize
UAF> show http$server /full
Username: HTTP$SERVER Owner: WASD Server
Account: UIC: [77,1] ([HTTP$SERVER])
CLI: DCL Tables: DCLTABLES
Default: DUA2:[HTTP$SERVER]
LGICMD: LOGIN.COM
Flags: DisNewMail DisMail
Primary days: Mon Tue Wed Thu Fri
Secondary days: Sat Sun
Primary 000000000011111111112222 Secondary 000000000011111111112222
Day Hours 012345678901234567890123 Day Hours 012345678901234567890123
Network: ##### Full access ###### ##### Full access ######
Batch: ##### Full access ###### ##### Full access ######
Local: ----- No access ------ ----- No access ------
Dialup: ----- No access ------ ----- No access ------
Remote: ----- No access ------ ----- No access ------
Expiration: (none) Pwdminimum: 6 Login Fails: 0
Pwdlifetime: 90 00:00 Pwdchange: (pre-expired)
Last Login: (none) (interactive), 6-NOV-2016 09:18 (non-interactive)
Maxjobs: 0 Fillm: 300 Bytlm: 5000000
Maxacctjobs: 0 Shrfillm: 0 Pbytlm: 0
Maxdetach: 0 BIOlm: 2000 JTquota: 4000
Prclm: 100 DIOlm: 1000 WSdef: 1000
Prio: 4 ASTlm: 2000 WSquo: 4000
Queprio: 0 TQElm: 100 WSextent: 20000
CPU: (none) Enqlm: 500 Pgflquo: 500000
Authorized Privileges:
NETMBX TMPMBX
Default Privileges:
NETMBX TMPMBX
Identifier Value Attributes
WASD_HTTP_SERVER %X80010003
UAF>
UAF> show http$nobody /full
Username: HTTP$NOBODY Owner: WASD Scripting
Account: UIC: [76,1] ([HTTP$NOBODY])
CLI: DCL Tables: DCLTABLES
Default: DUA2:[HTTP$NOBODY]
LGICMD: LOGIN.COM
Flags: DisNewMail DisMail
Primary days: Mon Tue Wed Thu Fri
Secondary days: Sat Sun
Primary 000000000011111111112222 Secondary 000000000011111111112222
Day Hours 012345678901234567890123 Day Hours 012345678901234567890123
Network: ##### Full access ###### ##### Full access ######
Batch: ----- No access ------ ----- No access ------
Local: ----- No access ------ ----- No access ------
Dialup: ----- No access ------ ----- No access ------
Remote: ----- No access ------ ----- No access ------
Expiration: (none) Pwdminimum: 6 Login Fails: 0
Pwdlifetime: 90 00:00 Pwdchange: (pre-expired)
Last Login: (none) (interactive), 5-NOV-2016 01:33 (non-interactive)
Maxjobs: 0 Fillm: 300 Bytlm: 500000
Maxacctjobs: 0 Shrfillm: 0 Pbytlm: 0
Maxdetach: 0 BIOlm: 2000 JTquota: 4000
Prclm: 100 DIOlm: 1000 WSdef: 1000
Prio: 4 ASTlm: 2000 WSquo: 4000
Queprio: 0 TQElm: 100 WSextent: 20000
CPU: (none) Enqlm: 500 Pgflquo: 500000
Authorized Privileges:
NETMBX TMPMBX
Default Privileges:
NETMBX TMPMBX
Identifier Value Attributes
WASD_HTTP_NOBODY %X80010004
UAF>
UAF>
UAF> show webroot /full
Username: WEBROOT Owner: WEB ROOT HTML FILES
Account: WEBROOT UIC: [200,236] ([WEBROOT])
CLI: DCL Tables: DCLTABLES
Default: DUA2:[WEBROOT]
LGICMD: LOGIN
Flags: Captive
Primary days: Mon Tue Wed Thu Fri
Secondary days: Sat Sun
No access restrictions
Expiration: (none) Pwdminimum: 6 Login Fails: 0
Pwdlifetime: (none) Pwdchange: (pre-expired)
Last Login: 5-NOV-2016 01:51 (interactive), (none) (non-interactive)
Maxjobs: 0 Fillm: 300 Bytlm: 32768
Maxacctjobs: 0 Shrfillm: 0 Pbytlm: 0
Maxdetach: 0 BIOlm: 40 JTquota: 4096
Prclm: 2 DIOlm: 40 WSdef: 256
Prio: 4 ASTlm: 40 WSquo: 512
Queprio: 0 TQElm: 40 WSextent: 1024
CPU: (none) Enqlm: 200 Pgflquo: 32768
Authorized Privileges:
Default Privileges:
UAF>
UAF> exit
%UAF-I-NOMODS, no modifications made to system authorization file
%UAF-I-NAFNOMODS, no modifications made to network proxy database
%UAF-I-RDBNOMODS, no modifications made to rights database
SYS$SYSROOT:[SYSEXE]
There are some fabulous folks at the comp.os.vms newsgroup that are always ready to help. For example, this post came in extremely useful for me when I was struggling with HTTP 403 errors.
Troubleshooting
The only stumble I had was with file and directory permissions. If you get "ERROR 403 - The requested action is not permitted." or "ERROR 404 - The requested resource could not be found." errors, remember WASD needs to be able to reach and read the HTML files for your website in a different account, as well as FAL area files, and make sure they at least have READ privileges for the World:
$ SET FILE/PROT=(W:R) DUA2:[WEBROOT...]*.*
$ SET FILE/PROT=(W:R) DUA2:[FAL$SERVER...]*.*
WASD writes its httpd Access Log to the .LOG directory wasd_root:[log]. Example:
DUA2:[WASD_ROOT.LOCAL] dir wasd_root:[log]
Directory WASD_ROOT:[LOG]
.WWW_HIDDEN;1 LOCALHOST_80_20161031_ACCESS.LOG;1 README.HTML;1
SANYALNET-VAX-SANYAL_80_20161031_ACCESS.LOG;1
Total of 4 files.
DUA2:[WASD_ROOT.LOG] cd sys$system
SYS$SYSROOT:[SYSEXE] mc authorize
UAF> show http$server /full
Username: HTTP$SERVER Owner: WASD Server
Account: UIC: [77,1] ([HTTP$SERVER])
CLI: DCL Tables: DCLTABLES
Default: DUA2:[HTTP$SERVER]
LGICMD: LOGIN.COM
Flags: DisNewMail DisMail
Primary days: Mon Tue Wed Thu Fri
Secondary days: Sat Sun
Primary 000000000011111111112222 Secondary 000000000011111111112222
Day Hours 012345678901234567890123 Day Hours 012345678901234567890123
Network: ##### Full access ###### ##### Full access ######
Batch: ##### Full access ###### ##### Full access ######
Local: ----- No access ------ ----- No access ------
Dialup: ----- No access ------ ----- No access ------
Remote: ----- No access ------ ----- No access ------
Expiration: (none) Pwdminimum: 6 Login Fails: 0
Pwdlifetime: 90 00:00 Pwdchange: (pre-expired)
Last Login: (none) (interactive), 6-NOV-2016 09:18 (non-interactive)
Maxjobs: 0 Fillm: 300 Bytlm: 5000000
Maxacctjobs: 0 Shrfillm: 0 Pbytlm: 0
Maxdetach: 0 BIOlm: 2000 JTquota: 4000
Prclm: 100 DIOlm: 1000 WSdef: 1000
Prio: 4 ASTlm: 2000 WSquo: 4000
Queprio: 0 TQElm: 100 WSextent: 20000
CPU: (none) Enqlm: 500 Pgflquo: 500000
Authorized Privileges:
NETMBX TMPMBX
Default Privileges:
NETMBX TMPMBX
Identifier Value Attributes
WASD_HTTP_SERVER %X80010003
UAF>
UAF> show http$nobody /full
Username: HTTP$NOBODY Owner: WASD Scripting
Account: UIC: [76,1] ([HTTP$NOBODY])
CLI: DCL Tables: DCLTABLES
Default: DUA2:[HTTP$NOBODY]
LGICMD: LOGIN.COM
Flags: DisNewMail DisMail
Primary days: Mon Tue Wed Thu Fri
Secondary days: Sat Sun
Primary 000000000011111111112222 Secondary 000000000011111111112222
Day Hours 012345678901234567890123 Day Hours 012345678901234567890123
Network: ##### Full access ###### ##### Full access ######
Batch: ----- No access ------ ----- No access ------
Local: ----- No access ------ ----- No access ------
Dialup: ----- No access ------ ----- No access ------
Remote: ----- No access ------ ----- No access ------
Expiration: (none) Pwdminimum: 6 Login Fails: 0
Pwdlifetime: 90 00:00 Pwdchange: (pre-expired)
Last Login: (none) (interactive), 5-NOV-2016 01:33 (non-interactive)
Maxjobs: 0 Fillm: 300 Bytlm: 500000
Maxacctjobs: 0 Shrfillm: 0 Pbytlm: 0
Maxdetach: 0 BIOlm: 2000 JTquota: 4000
Prclm: 100 DIOlm: 1000 WSdef: 1000
Prio: 4 ASTlm: 2000 WSquo: 4000
Queprio: 0 TQElm: 100 WSextent: 20000
CPU: (none) Enqlm: 500 Pgflquo: 500000
Authorized Privileges:
NETMBX TMPMBX
Default Privileges:
NETMBX TMPMBX
Identifier Value Attributes
WASD_HTTP_NOBODY %X80010004
UAF>
UAF>
UAF> show webroot /full
Username: WEBROOT Owner: WEB ROOT HTML FILES
Account: WEBROOT UIC: [200,236] ([WEBROOT])
CLI: DCL Tables: DCLTABLES
Default: DUA2:[WEBROOT]
LGICMD: LOGIN
Flags: Captive
Primary days: Mon Tue Wed Thu Fri
Secondary days: Sat Sun
No access restrictions
Expiration: (none) Pwdminimum: 6 Login Fails: 0
Pwdlifetime: (none) Pwdchange: (pre-expired)
Last Login: 5-NOV-2016 01:51 (interactive), (none) (non-interactive)
Maxjobs: 0 Fillm: 300 Bytlm: 32768
Maxacctjobs: 0 Shrfillm: 0 Pbytlm: 0
Maxdetach: 0 BIOlm: 40 JTquota: 4096
Prclm: 2 DIOlm: 40 WSdef: 256
Prio: 4 ASTlm: 40 WSquo: 512
Queprio: 0 TQElm: 40 WSextent: 1024
CPU: (none) Enqlm: 200 Pgflquo: 32768
Authorized Privileges:
Default Privileges:
UAF>
UAF> exit
%UAF-I-NOMODS, no modifications made to system authorization file
%UAF-I-NAFNOMODS, no modifications made to network proxy database
%UAF-I-RDBNOMODS, no modifications made to rights database
SYS$SYSROOT:[SYSEXE]
There are some fabulous folks at the comp.os.vms newsgroup that are always ready to help. For example, this post came in extremely useful for me when I was struggling with HTTP 403 errors.
No comments:
Post a Comment
"SEO" link builders: move on, your spam link will not get posted.
Note: Only a member of this blog may post a comment.