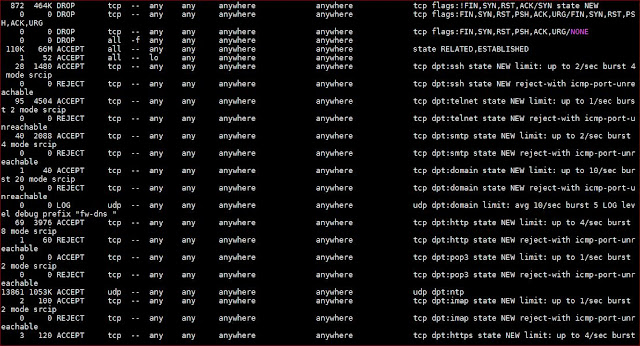
I use iptables to secure my Linux-based internet-facing hobbyist servers. The current iptables, residing at one of these servers (sanyalnet-cloud-vps2.freeddns.org) at /etc/sysconfig/iptables, is as below.
This particular server runs on CentOS 7. The iptables rules provide basic network exploit protection from syn flood, nul, christmas and fragmented packets and adds rate-limited DDOS flood protection for ssh, telnet, smtp, dns, http, pop3, ntp, IMAP, https, smtps, starttls, imap-ssl/tls, pop-ssl/tls, dovecot, sieve, managesieve, DECnet bridge (HECnet), stunnel, syslog etc. ports that are usual for any internet-facing server providing public services. It has the following open ports for the services it provides:
- ssh
- telnet, forwarded to CLOUDY VAX - the hosted DECVAX-11/780 SIMH simulated Digital VAX server running OpenVMS 7.3
- SMTP (authenticated, not public)
- DNS - this DNS server blocks advertising and tracking websites as well as malware
- http - a basic static web-site is hosted on this server; also reachable over the TOR network at fz2koi5kviaph4bl.onion)
- POP (authenticated, not public)
- NTP - this server is an official stratum-2 public NTP server listed ntp.org and is a member of the NTP Pool Project
- IMAP (authenticated, not public)
- https (currently unused)
- STARTTLS / SMTPS (authenticated, not public)
- IMAP SSL/TLS (authenticated, not public)
- POP SSL/TLS (authenticated, not public)
- Dovecot Sieve / ManageSieve
- DECnet bridge connecting QCOCAL (SIMH MicroVAX 3900/OpenVMS 7.3 at home), JUICHI (SIMH DEC PDP-11/24 RSX-11M PLUS at home) and CLOUDY VAX (SIMH VAX-11/780 OpenVMS 7.3) to HECnet the global hobbyist DECnet network
- TOR Proxy service (authenticated, not public)
- stunnel (secure tunnel) service to syslog daemon for encrypted remote logging
- syslog
- TOR relay node (this server is a TOR relay-only node, not a TOR exit node; no TOR traffic is logged at all on this server)
No comments:
Post a Comment
"SEO" link builders: move on, your spam link will not get posted.
Note: Only a member of this blog may post a comment.